Bloomberg Government News
Breaking the stories public affairs professionals need to know with unlimited coverage of key policy and developing legislation.
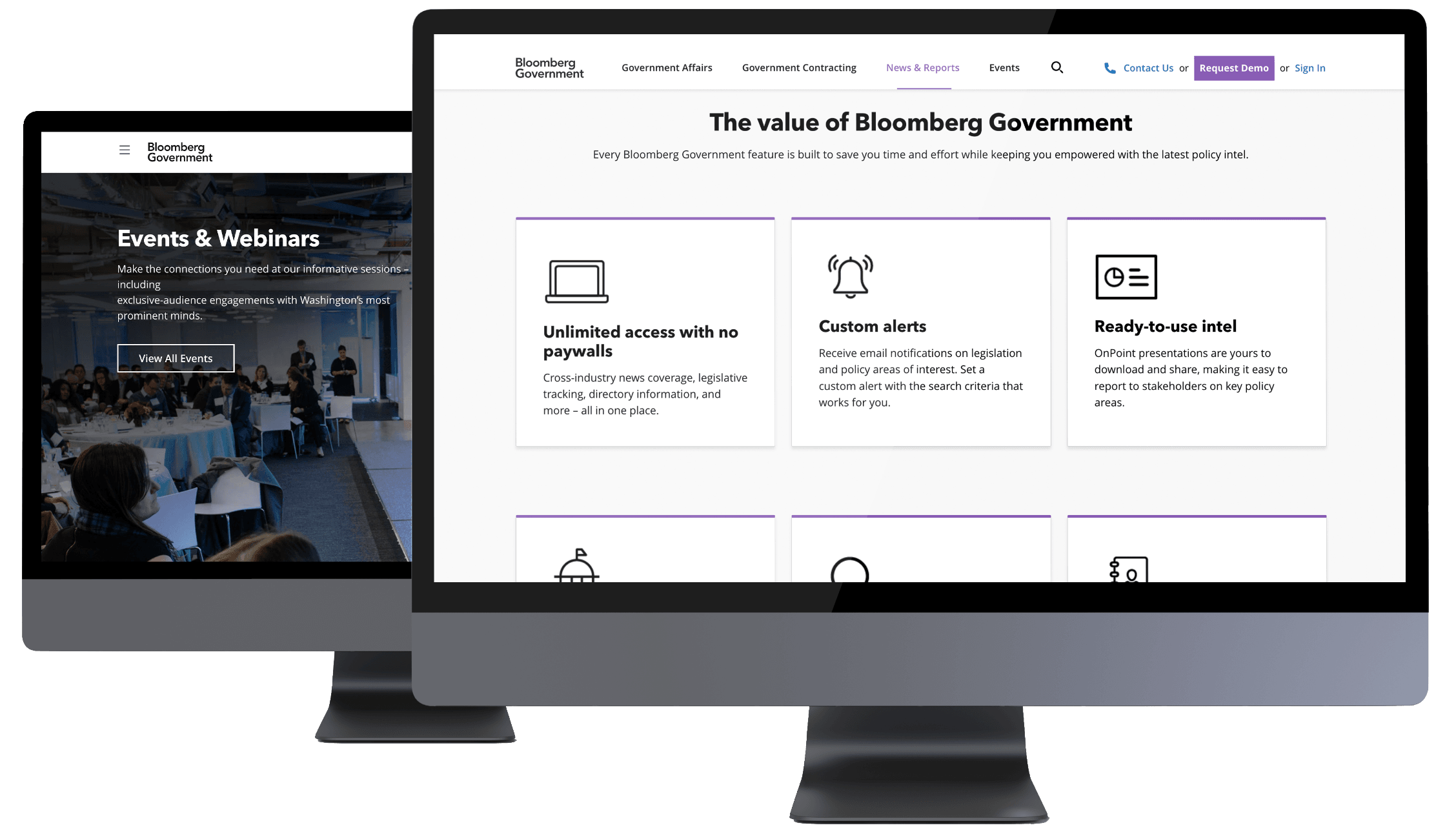
Bloomberg Government is your one stop for intelligence on developing federal and state policy, trusted news straight from Congress and around the nation, expert analysis, bill tracking, and more.
Original news and exclusive content
Our reporters work where news happens – keeping you informed directly from Capitol Hill, state capitols, courtrooms, and agencies. Plus, customizable access to over 35,000 national and state news sources and ready-to-use presentations on key policy initiatives, ensures you get the news first and understand the impacts.
Coverage that’s tailored to you
Finding relevant intel on the key issues you’re following has never been easier. BGOV lets you swiftly and accurately locate precise information on the topics that matter most to you. With customized alerts delivered straight to your inbox, AI-powered advanced search functions, and comprehensive social media monitoring capabilities, you have full control over how and when you receive news, content, and updates on topics you choose.
Reporting that covers every policy area at every level
No matter where you focus, we’ve got you covered. We keep you informed on every policy area at both the federal and state levels. Our team of reporters and industry experts are always in the room on Capitol Hill and across the nation, sending immediate and in-depth information to help you make informed and strong decisions.
Deep, thoughtful analysis and guidance.
Rely on our collection of special reports and white papers for a complete, expert look at some of the most pressing challenges for government professionals.
Legislative tracking that leads the industry for federal and state
Keep your finger on the pulse of what’s happening at each stage of legislation. With our unmatched federal and state legislative tracking, you can follow legislation through every policy movement with exclusive federal bill summaries, comprehensive coverage of markups, regulatory comment trackers, and more.
Learn more about a Bloomberg Government subscription
Our popular newsletters provide the latest news, analysis, reports, and more straight to your inbox.

What to Know in Washington
Get a head start on the day with reporting on the most important stories from Congress, the administration, and beyond.
States of Play Newsletter
A daily round-up of key news from state capitols across the country helps you easily track local policy trends across jurisdictions.
Ready to stay ahead?
Legislation will always move fast, and with Bloomberg Government, you will too. Set up an in-person or virtual product demonstration today.
